In the ever-evolving landscape of cloud computing, the need for automation and governance at scale has never been more critical. Microsoft Azure, a leading cloud service provider, offers many features to manage and secure cloud resources effectively. However, the real game-changer in this domain is the Cloud Adoption Framework (CAF) Enterprise Scale Rover, a tool designed to supercharge your Azure governance strategy. This blog post will delve into automating the deployment of Azure Policy Definitions, Policy Sets (Initiatives), and Policy Assignments using CAF Enterprise Scale Rover, ensuring your Azure environment remains compliant, secure, and optimized.
Introduction to Azure Policies and CAF Rover
Azure Policies play a pivotal role in the governance framework of Azure environments. They enable organizations to define, assign, and manage policies that enforce rules over their resources, ensuring compliance with company standards and regulatory requirements. While Azure Policies are powerful, managing them across a large-scale environment can be daunting.
Enter CAF Enterprise Scale Rover, an innovative solution that streamlines the deployment and management of Azure Policies. It is designed to automate the process, making it easier, faster, and more efficient. By leveraging the CAF Rover, IT professionals can focus on strategic tasks, leaving the heavy lifting to the automation processes.
Setting Up Your Environment for CAF Rover
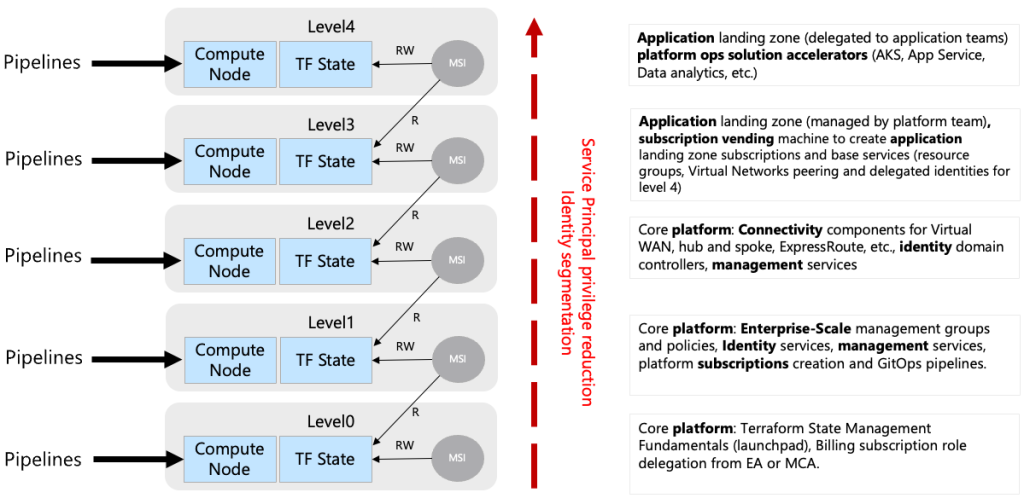
Before diving into the automation process, it’s essential to set up your environment to run the CAF Rover. This setup involves ensuring your development environment is ready, installing necessary tools like Docker, Terraform, Git, and configuring VSCode with specific extensions for Azure Policy and Docker support. Detailed guidance on setting up your environment can be found in the provided recommended reading, highlighting the importance of a properly configured dev environment for a seamless automation experience.
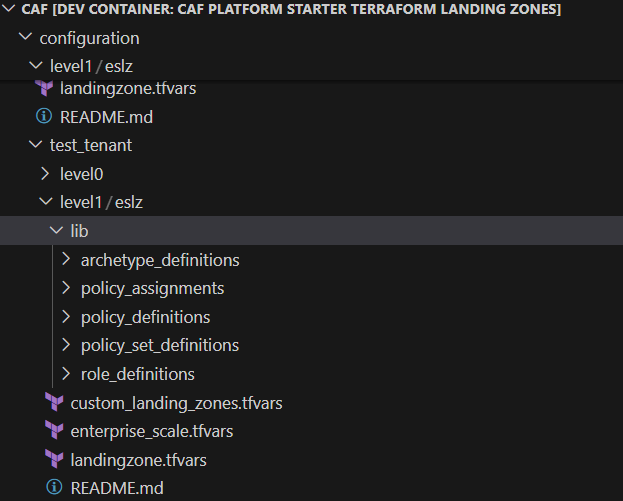
You must plan out your Policy Definitions, then group them into Initiatives, and then assign initiatives to scopes (Management Groups or Subscriptions).
Automating Policy Definitions Deployment
The journey begins with automating Policy Definitions, the cornerstone of Azure Policy management. CAF Rover simplifies this process by leveraging a structured JSON format for defining policies, focusing on key areas such as allowed regions, naming conventions, and resource compliance checks. The process entails writing your Policy Definition in JSON, committing it to your Git repository, and deploying it to your Azure environment via CAF Rover commands. This approach ensures that all your cloud resources adhere to defined governance standards from the get-go.
Sample Policy Definition
{
"name": "Append-AppService-httpsonly",
"type": "Microsoft.Authorization/policyDefinitions",
"apiVersion": "2021-06-01",
"scope": null,
"properties": {
"policyType": "Custom",
"mode": "All",
"displayName": "AppService append enable https only setting to enforce https setting.",
"description": "Appends the AppService sites object to ensure that HTTPS only is enabled for server/service authentication and protects data in transit from network layer eavesdropping attacks. Please note Append does not enforce compliance use then deny.",
"metadata": {
"version": "1.0.0",
"category": "App Service",
"source": "https://github.com/Azure/Enterprise-Scale/",
"alzCloudEnvironments": [
"AzureCloud",
"AzureChinaCloud",
"AzureUSGovernment"
]
},
"parameters": {
"effect": {
"type": "String",
"defaultValue": "Append",
"allowedValues": [
"Audit",
"Append",
"Disabled"
],
"metadata": {
"displayName": "Effect",
"description": "Enable or disable the execution of the policy"
}
}
},
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.Web/sites"
},
{
"field": "Microsoft.Web/sites/httpsOnly",
"notequals": true
}
]
},
"then": {
"effect": "[parameters('effect')]",
"details": [
{
"field": "Microsoft.Web/sites/httpsOnly",
"value": true
}
]
}
}
}
}Streamlining Policy Sets (Initiatives) Deployment
Next, we focus on Policy Sets, also known as Initiatives, which group multiple Policy Definitions for cohesive management. The CAF Rover enhances the deployment of Policy Sets by automating their creation and assignment. By grouping related policies, you can ensure comprehensive coverage of governance requirements, such as naming conventions and compliance checks, across your Azure resources. The automation process involves defining your Policy Sets in JSON format, committing them to your repository, and deploying them through CAF Rover, streamlining the governance of your cloud environment.
Sample Policy Set (Initiative)
{
"name": "Audit-UnusedResourcesCostOptimization",
"type": "Microsoft.Authorization/policySetDefinitions",
"apiVersion": "2021-06-01",
"scope": null,
"properties": {
"policyType": "Custom",
"displayName": "Unused resources driving cost should be avoided",
"description": "Optimize cost by detecting unused but chargeable resources. Leverage this Azure Policy Initiative as a cost control tool to reveal orphaned resources that are contributing cost.",
"metadata": {
"version": "2.0.0",
"category": "Cost Optimization",
"source": "https://github.com/Azure/Enterprise-Scale/",
"alzCloudEnvironments": [
"AzureCloud",
"AzureChinaCloud",
"AzureUSGovernment"
]
},
"parameters": {
"effectDisks": {
"type": "String",
"metadata": {
"displayName": "Disks Effect",
"description": "Enable or disable the execution of the policy for Microsoft.Compute/disks"
},
"allowedValues": [
"Audit",
"Disabled"
],
"defaultValue": "Audit"
},
"effectPublicIpAddresses": {
"type": "String",
"metadata": {
"displayName": "PublicIpAddresses Effect",
"description": "Enable or disable the execution of the policy for Microsoft.Network/publicIpAddresses"
},
"allowedValues": [
"Audit",
"Disabled"
],
"defaultValue": "Audit"
},
"effectServerFarms": {
"type": "String",
"metadata": {
"displayName": "ServerFarms Effect",
"description": "Enable or disable the execution of the policy for Microsoft.Web/serverfarms"
},
"allowedValues": [
"Audit",
"Disabled"
],
"defaultValue": "Audit"
}
},
"policyDefinitions": [
{
"policyDefinitionReferenceId": "AuditDisksUnusedResourcesCostOptimization",
"policyDefinitionId": "${current_scope_resource_id}/providers/Microsoft.Authorization/policyDefinitions/Audit-Disks-UnusedResourcesCostOptimization",
"parameters": {
"effect": {
"value": "[parameters('effectDisks')]"
}
},
"groupNames": []
},
{
"policyDefinitionReferenceId": "AuditPublicIpAddressesUnusedResourcesCostOptimization",
"policyDefinitionId": "${current_scope_resource_id}/providers/Microsoft.Authorization/policyDefinitions/Audit-PublicIpAddresses-UnusedResourcesCostOptimization",
"parameters": {
"effect": {
"value": "[parameters('effectPublicIpAddresses')]"
}
},
"groupNames": []
},
{
"policyDefinitionReferenceId": "AuditServerFarmsUnusedResourcesCostOptimization",
"policyDefinitionId": "${current_scope_resource_id}/providers/Microsoft.Authorization/policyDefinitions/Audit-ServerFarms-UnusedResourcesCostOptimization",
"parameters": {
"effect": {
"value": "[parameters('effectServerFarms')]"
}
},
"groupNames": []
},
{
"policyDefinitionReferenceId": "AuditAzureHybridBenefitUnusedResourcesCostOptimization",
"policyDefinitionId": "${current_scope_resource_id}/providers/Microsoft.Authorization/policyDefinitions/Audit-AzureHybridBenefit",
"parameters": {
"effect": {
"value": "Audit"
}
},
"groupNames": []
}
],
"policyDefinitionGroups": null
}
}
Automating Policy Assignments
The final piece of the automation puzzle is Policy Assignments. This step activates the policies, applying them to your Azure resources. CAF Rover facilitates the automation of both custom and built-in Policy Assignments, ensuring your resources are governed according to the defined policies. Whether you are assigning custom initiatives or leveraging Azure’s built-in policies for zone resilience, the process is simplified through automation, allowing for efficient and effective governance at scale.
Sample Policy Assignment
{
"type": "Microsoft.Authorization/policyAssignments",
"apiVersion": "2022-06-01",
"name": "as_baseline_security",
"dependsOn": [],
"properties": {
"description": "This assignment includes EDG baseline security policies.",
"displayName": "Custom baseline security",
"policyDefinitionId": "${current_scope_resource_id}/providers/Microsoft.Authorization/policySetDefinitions/custom_baseline_security",
"enforcementMode": null,
"metadata": {
},
"nonComplianceMessages": [
{
"policyDefinitionReferenceId": "custom_audit_function_app_require_msi_tf_1",
"message": "FUNC-001 - Use Azure-managed identity to securely authenticate to other cloud services/resources"
},
{
"policyDefinitionReferenceId": "custom_deny_function_app_remotedebugging_tf_1",
"message": "FUNC-014 - Turn off Remote debugging on your Function apps"
},
{
"policyDefinitionReferenceId": "custom_deny_mismatched_res_resgroup_locations_tf_1",
"message": "AZ-001 - Resource has been deployed in a different location from the resource group containing it"
},
{
"policyDefinitionReferenceId": "custom_deny_non_allowed_resource_locations_tf_1",
"message": "AZ-002 - Resource has been deployed in an unauthorised location"
},
{
"policyDefinitionReferenceId": "custom_deny_storage_acc_accessible_over_http_tf_1",
"message": "ST-013 - Enforce data encryption in transit by enabling HTTPS only"
},
{
"policyDefinitionReferenceId": "custom_deny_storage_acc_disable_public_network_tf_1",
"message": "ST-001 - Disable public network access"
},
{
"policyDefinitionReferenceId": "custom_deploy_function_app_accessible_over_http_tf_1",
"message": "FUNC-003 - Enforce data encryption in transit by enabling HTTPS only"
},
{
"policyDefinitionReferenceId": "custom_deploy_function_app_require_ftps_only_tf_1",
"message": "FUNC-009 - Disable FTP based deployment or configure to accept FTPS only"
},
{
"policyDefinitionReferenceId": "custom_deploy_function_app_require_tls12_tf_1",
"message": "FUNC-004 - Enforce minimum TLS version to 1.2"
}
],
"parameters": {
},
"scope": "${current_scope_resource_id}",
"notScopes": []
},
"location": "${default_location}",
"identity": {
"type": "SystemAssigned"
}
}
Archetypes
Archetypes are used in the Azure landing zone conceptual architecture to describe the Landing Zone configuration using a template-driven approach. The archetype is what fundamentally transforms Management Groups and Subscriptions into Landing Zones.
An archetype defines which Azure Policy and Access control (IAM) settings are needed to secure and configure the Landing Zones with everything needed for safe handover to the Landing Zone owner. This covers critical platform controls and configuration items, such as:
- Consistent role-based access control (RBAC) settings
- Guardrails for security settings
- Guardrails for common workload configurations (e.g. SAP, AKS, WVD, etc.)
- Automate provisioning of critical platform resources such as monitoring and networking solutions in each Landing Zone
This approach provides improved autonomy for application teams, whilst ensuring security policies and standards are enforced.
Why using CAF rover?
This tool greatly simplifies secure state management on Azure storage accounts. Additionally, it helps with testing different versions of binaries such as new versions of Terraform, Azure CLI, jq, tflint, etc. This tool also provides a ubiquitous development environment, which means everyone works with the same versions of the DevOps toolchain, always up-to-date, and runs on laptops, pipelines, GitHub Codespaces, and other platforms. It also facilitates the identity transition to any CI/CD, as all CI/CD have container capabilities. This tool allows for easy transition from one DevOps environment to another, including GitHub Actions, Azure DevOps, Jenkins, CircleCI, etc. Lastly, it’s an open-source tool and leverages open-source projects that are often needed with Terraform.
- Helps testing different versions of binaries (new version of Terraform, Azure CLI, jq, tflint etc.)
- Ubiquitous development environment: everyone works with the same versions of the DevOps toolchain, always up-to-date, running on laptop, pipelines, GitHub Codespaces, etc.
- Facilitates the identity transition to any CI/CD: namely all CI/CD have container capabilities.
- Allows easy transition from one DevOps environment to another (GitHub Actions, Azure DevOps, Jenkins, CircleCI etc.)
- It’s open-source and leveraging open-source projects that you often need with Terraform.
Integrating with Azure DevOps Pipelines
A critical aspect of automating Azure Policy deployment using CAF Enterprise Scale Rover is its seamless integration with Azure DevOps pipelines. This integration enables organizations to adopt a DevOps approach to cloud governance, where policy changes are version-controlled, reviewed, and deployed through automated CI/CD pipelines. By incorporating CAF Rover into Azure DevOps pipelines, you can ensure that policy deployments are consistent, repeatable, and auditable across different environments. This process not only enhances governance and compliance but also aligns with best practices for Infrastructure as Code (IaC), facilitating a collaborative and efficient workflow among development, operations, and security teams. Leveraging Azure DevOps pipelines with CAF Rover automation empowers organizations to maintain a high governance standard while embracing the agility and speed that cloud environments offer.
Conclusion
Automating the deployment of Azure Policy Definitions, Policy Sets (Initiatives), and Policy Assignments using CAF Enterprise Scale Rover represents a significant leap forward in cloud governance. This approach not only saves time and reduces the potential for human error but also ensures a consistent and compliant Azure environment. By embracing automation with CAF Rover, organizations can achieve a robust governance framework that scales with their Azure deployments, securing their cloud journey’s success.
For those keen to automate their Azure Policies, diving into the CAF Rover’s capabilities is a must. The combination of detailed documentation, structured JSON for policy definitions, and automated deployment processes provides a clear path to efficient and effective Azure governance. Embrace the power of automation with CAF Enterprise Scale Rover and take your Azure governance to the next level.
Recommended Reading
https://aztfmod.github.io/documentation/docs/rover/rover-intro